A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of Internet traffic. These attacks leverage multiple compromised computer systems as sources of attack traffic. The resulting flood of incoming messages, connection requests, or malformed packets to the target system forces it to slow down or even crash and shut down, thereby denying service to legitimate users.
DDoS attacks can be categorized into three types:
- Volume-Based Attacks: These involve overwhelming the bandwidth of the target site with high volumes of traffic.
- Protocol Attacks: These focus on exploiting server resources or intermediate communication equipment like firewalls and load balancers.
- Application Layer Attacks: These target specific applications or services, making them unavailable to users.
Understanding the nature of DDoS attacks is crucial for implementing effective anti-DDoS protection strategies.

What is Anti-DDoS?
Anti-DDoS refers to a set of tools, services, and strategies designed to protect against DDoS attacks. These solutions detect and mitigate DDoS attacks, ensuring the availability and reliability of services. Anti-DDoS solutions can be hardware-based, software-based, or cloud-based, and they often include features like traffic analysis, rate limiting, and automated response mechanisms.
Key components of anti-DDoS solutions include:
- Detection Mechanisms: To identify potential DDoS traffic patterns.
- Mitigation Strategies: To filter out malicious traffic while allowing legitimate traffic to pass through.
- Reporting Tools: To provide insights into attack vectors and effectiveness of mitigation.
Implementing robust anti-DDoS protection is essential for maintaining service availability and protecting organizational reputation.
Benefits & ROI of Anti-DDoS Protection
Investing in anti-DDoS protection offers numerous benefits, both in terms of security and financial returns. The primary advantage is the assurance of service availability, which is critical for maintaining customer trust and business continuity.
Key benefits include:
- Enhanced Security: Protection against a wide range of DDoS attacks.
- Business Continuity: Minimizing downtime ensures uninterrupted services.
- Cost Savings: Preventing attacks can save significant costs associated with downtime and recovery.
- Customer Trust: Reliable services enhance customer satisfaction and loyalty.
Return on Investment (ROI):
Calculating the ROI of anti-DDoS solutions involves comparing the cost of implementing the protection against the potential losses from DDoS attacks. Factors to consider include:
- Potential Revenue Loss: Due to service downtime.
- Recovery Costs: Expenses related to restoring services post-attack.
- Reputation Damage: Long-term impact on brand image.
By preventing even a single significant DDoS attack, organizations can justify the investment in anti-DDoS solutions.
2025 DDoS Threat Landscape
The threat landscape in 2025 has evolved, with DDoS attacks becoming more sophisticated and frequent. Attackers are leveraging advanced techniques and exploiting vulnerabilities in emerging technologies.
Key statistics:
- Increase in Attack Frequency: A significant rise in the number of DDoS attacks compared to previous years.
- Higher Attack Volumes: Attacks are now capable of generating traffic volumes exceeding 1 Tbps.
- Target Diversification: Not just large enterprises, but small and medium businesses are increasingly targeted.
Emerging Threats:
- IoT Exploitation: Compromised IoT devices are being used to launch large-scale attacks.
- AI-Powered Attacks: Use of artificial intelligence to adapt and evade traditional defense mechanisms.
- Multi-Vector Attacks: Combining different attack methods to overwhelm defenses.
How Anti-DDoS Works (Layer-by-Layer)
Anti-DDoS solutions operate across various layers of the OSI model to detect and mitigate attacks effectively.
Layer-wise breakdown:
- Network Layer (Layer 3): Focuses on filtering out malicious IP addresses and blocking volumetric attacks.
- Transport Layer (Layer 4): Monitors and controls traffic based on TCP/UDP protocols to prevent SYN floods.
- Application Layer (Layer 7): Protects against attacks targeting specific applications, such as HTTP floods.
Mitigation Techniques:
- Rate Limiting: Controls the rate of incoming requests to prevent overwhelming the server.
- Traffic Analysis: Identifies abnormal traffic patterns indicative of an attack.
- Challenge-Response Tests: Uses CAPTCHAs or similar methods to distinguish between bots and legitimate users.
Implementing a multi-layered defense strategy enhances the effectiveness of anti-DDoS protection.
Anti-DDoS Program, Software & Tool Comparison
Selecting the right anti-DDoS solution involves evaluating various programs, software, and tools based on organizational needs.
| Solution | Type | Features | Ideal For |
|---|---|---|---|
| Sangfor Network Secure | Hardware/Cloud | Comprehensive L2–L7 protection, AI-based threat detection, integrated WAF, IPS, and anti-virus | Enterprises seeking integrated security solutions |
| Cloudflare | Cloud-based | Real-time traffic analysis, CDN | Websites and APIs |
| Imperva | Cloud-based | Advanced bot protection, analytics | Enterprises |
| AWS Shield | Cloud-based | Integration with AWS services | AWS-hosted applications |
| Sucuri | Cloud-based | Website firewall, malware scanning | Small to medium websites |
| Radware | Hardware/Cloud | Behavioral-based detection | Large enterprises |
Considerations:
- Scalability: Ability to handle increasing traffic loads.
- Integration: Compatibility with existing infrastructure.
- Support: Availability of customer support and response times.
Anti-DDoS for Dedicated Servers
Dedicated servers require specialized anti-DDoS solutions to safeguard against targeted attacks. These servers often host critical applications and services, making them prime targets for attackers.
Protection Strategies:
- Hardware Appliances: Deploying on-premises devices that filter malicious traffic.
- Cloud-Based Services: Redirecting traffic through cloud scrubbing centers.
- Hybrid Approaches: Combining both hardware and cloud solutions for comprehensive protection.
Benefits:
- Enhanced Performance: Dedicated resources ensure minimal latency.
- Customization: Tailored configurations to meet specific security needs.
- Reliability: Reduced risk of collateral damage from attacks targeting shared resources.
Implementing robust anti-DDoS measures for dedicated servers is crucial for maintaining service integrity.
Continuing from the previous sections, here are the expanded portions of the article:
Key Features, SLAs & Cost Models
When evaluating anti-DDoS solutions, it's crucial to understand the key features they offer, the Service Level Agreements (SLAs) they provide, and the associated cost models. These factors determine the effectiveness, reliability, and affordability of the protection.
Key Features:
- Real-time Monitoring: Continuous surveillance of network traffic to detect anomalies indicative of DDoS attacks.
- Automated Mitigation: Immediate response mechanisms that activate upon detecting an attack, minimizing downtime.
- Scalability: Ability to handle increasing volumes of traffic without compromising performance.
- Customization: Configurable settings to tailor protection according to specific organizational needs.
Service Level Agreements (SLAs):
SLAs define the expected performance and responsibilities of the service provider. Key SLA metrics include:
- Time to Detect: The duration between the onset of an attack and its detection.
- Time to Mitigate: The time taken to neutralize the attack after detection.
- Uptime Guarantee: The percentage of time the service is guaranteed to be operational.
- Support Response Time: The maximum time within which support will respond to incidents.
Cost Models:
Understanding the pricing structure is vital for budgeting and ensuring cost-effectiveness.
- Flat-rate Pricing: A fixed monthly or annual fee regardless of usage.
- Usage-based Pricing: Charges based on the volume of traffic or number of attacks mitigated.
- Tiered Pricing: Different packages offering varying levels of protection and features.
Evaluating these aspects helps in selecting an anti-DDoS solution that aligns with both security requirements and financial constraints.
Implementation Roadmap & Best Practices
Implementing an effective anti-DDoS strategy involves a systematic approach and adherence to best practices to ensure robust protection. By following structured guidelines and utilizing powerful tools, organizations can significantly enhance their resilience against evolving DDoS threats.
Implementation Roadmap:
- Assessment: Evaluate current infrastructure thoroughly to identify vulnerabilities and potential attack vectors. Comprehensive assessments help in understanding the scope and scale of protection required.
- Planning: Develop a detailed DDoS response plan, clearly outlining roles, responsibilities, escalation paths, and communication procedures. An organized approach ensures timely and coordinated responses during attacks.
- Solution Selection: Choose an anti-DDoS solution that aligns with organizational security needs, integrates seamlessly with existing infrastructure, and offers scalability for future growth.
- Deployment: Implement the selected solution with proper configuration, comprehensive testing, and validation procedures. Ensure settings are optimized to the organization's specific network traffic patterns and risk profile.
- Monitoring: Continuously monitor network traffic and system performance using advanced analytics to promptly detect and respond to DDoS threats.
Best Practices:
- Regular Updates: Maintain up-to-date systems and security measures to protect against known vulnerabilities. Regularly updating software, firmware, and policies helps prevent exploitation of security gaps.
- Employee Training: Conduct ongoing training sessions to educate staff on recognizing, preventing, and responding effectively to DDoS attacks.
- Redundancy: Implement redundant and distributed systems to ensure service continuity and minimize downtime during attacks.
- Incident Response Plan: Maintain a comprehensive, well-documented, and regularly tested incident response plan to manage DDoS attacks effectively and minimize impact.
Sangfor Network Secure Platform:
Sangfor Network Secure Platform provides organizations with an integrated, user-friendly, and powerful security solution designed to combat multiple threat vectors, including comprehensive DDoS protection. Key features include:
- DoS/DDoS Protection: Robust inbound and outbound attack prevention mechanisms that mitigate various types of DDoS attacks, ensuring continuous network availability.
- Integrated Security Modules: Combines firewall capabilities, intrusion prevention systems (IPS), anti-virus protection, and web application firewall (WAF) into a unified security architecture.
- AI-Powered Threat Detection: Leverages advanced artificial intelligence technologies such as Engine Zero and Neural-X to deliver proactive threat detection and real-time analytics.
- User-Friendly Management: Offers a simplified, intuitive user interface that facilitates rapid configuration, real-time monitoring, and streamlined maintenance.
Below is a practical example showcasing how to configure an anti-DDoS policy within the Sangfor Network Secure Platform:
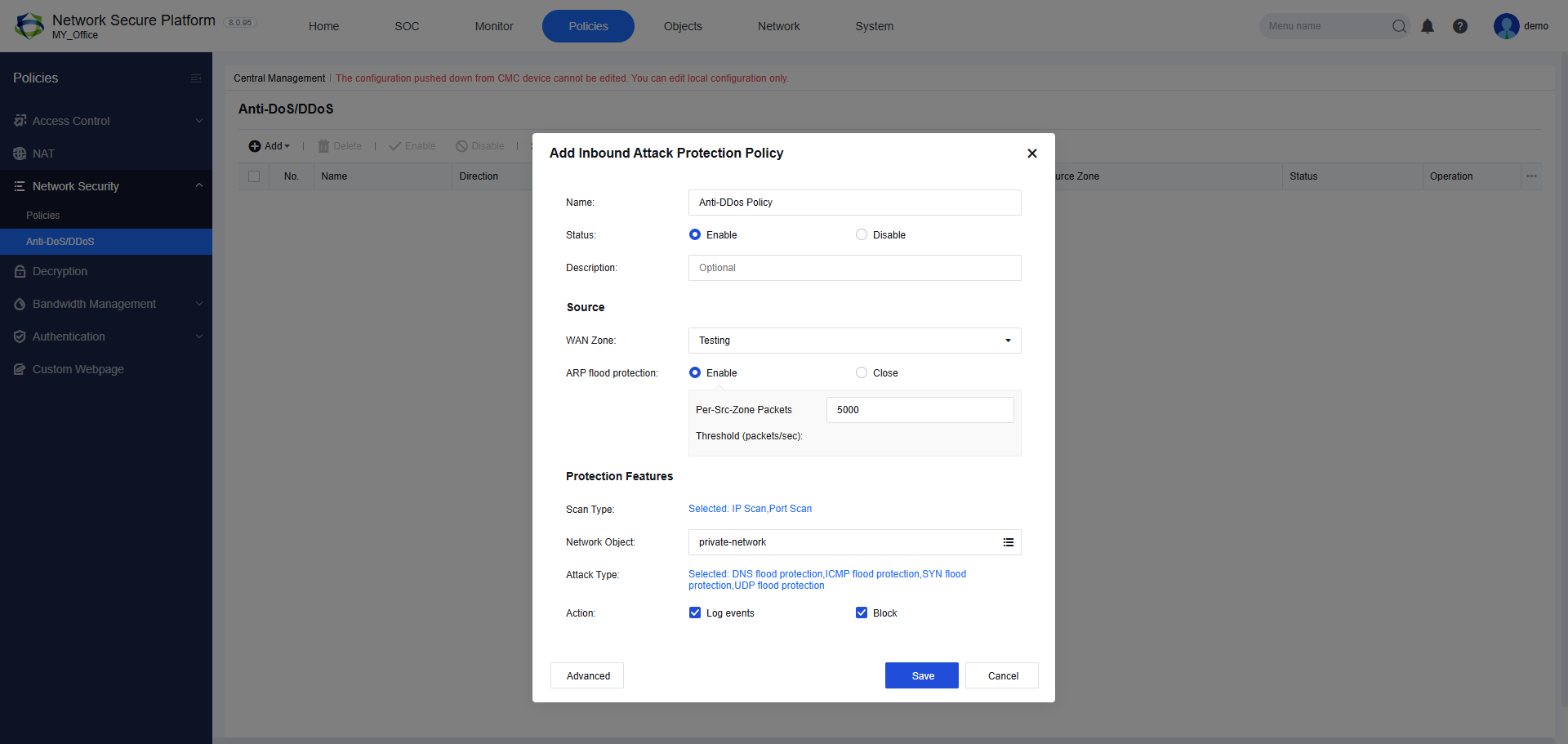
In this configuration interface, administrators can:
- Define clear policy names and quickly toggle policies on or off.
- Set ARP flood protection thresholds to mitigate ARP-based flooding attacks.
- Specify protection types against DNS flood, ICMP flood, SYN flood, and UDP flood attacks, among other common threats.
- Easily select and manage protected network segments, enhancing targeted protection.
- Implement logging and automatic blocking actions to swiftly mitigate malicious traffic.
The intuitive interface of Sangfor Network Secure Platform ensures effective and rapid policy deployment, enabling organizations to respond proactively and maintain robust protection against evolving DDoS threats.
Conclusion & Next Steps
In the evolving landscape of cybersecurity threats, implementing robust anti-DDoS protection is no longer optional but a necessity. By understanding the nature of DDoS attacks, evaluating appropriate solutions, and adhering to best practices, organizations can safeguard their digital assets and ensure uninterrupted service delivery.
Next Steps:
- Assessment: Evaluate your current infrastructure for vulnerabilities.
- Planning: Develop a comprehensive DDoS response strategy.
- Implementation: Deploy suitable anti-DDoS solutions tailored to your needs.
- Monitoring: Continuously monitor network traffic and system performance.
- Review: Regularly update your response plans to adapt to emerging threats.
Taking these proactive measures will enhance your organization's resilience against DDoS attacks and contribute to overall cybersecurity posture.
Frequently Asked Questions
Anti-DDoS software solutions are applications that monitor and filter traffic to prevent DDoS attacks, often deployed on existing infrastructure. Hardware solutions involve dedicated devices installed within the network to detect and mitigate attacks. The choice depends on factors like network size, budget, and specific security requirements.
Absolutely. Small businesses are increasingly targeted by cyberattacks due to perceived vulnerabilities. Implementing anti-DDoS measures helps protect their online presence, maintain customer trust, and prevent potential financial losses.
Properly configured anti-DDoS solutions are designed to minimize impact on legitimate traffic, ensuring that website performance remains unaffected during normal operations. During an attack, these solutions work to maintain service availability by filtering malicious traffic.
Combining on-premises and cloud-based solutions can provide comprehensive protection. On-premises solutions offer immediate response capabilities, while cloud-based services provide scalability to handle large-scale attacks.
DDoS response plans should be reviewed and updated regularly, at least annually or after any significant changes in infrastructure or threat landscape, to ensure effectiveness and relevance.





