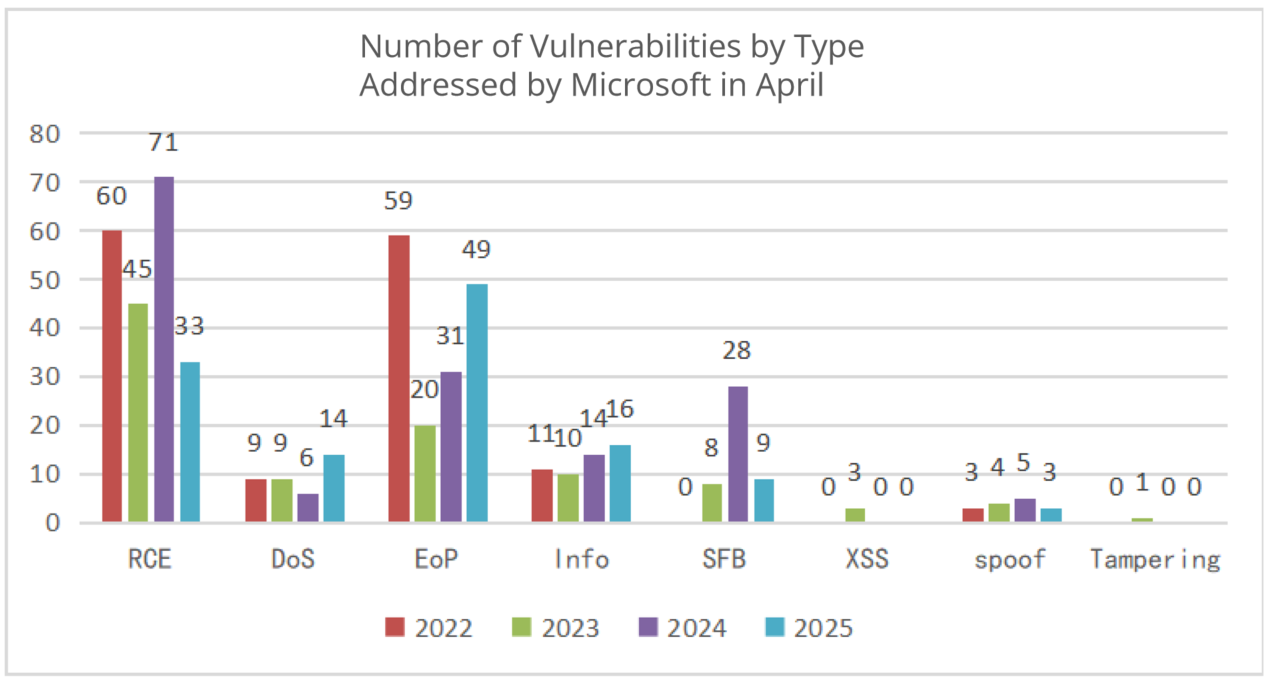
Earth Day, held annually on April 22, is one of the largest global movements dedicated to environmental action. This year, Earth Day 2025 is centered around the theme OUR POWER, OUR PLANET, inviting global unity behind renewable energy and aiming to triple the generation of clean electricity worldwide by 2030. EarthDay.org calls everyone to participate actively in Earth Action Day by educating, advocating, mobilizing, pledging action online, attending local events, integrating sustainability lessons, and donating to support efforts.
Robust cybersecurity and efficient cloud computing are vital in facilitating sustainability across industries crucial to societal functioning, such as logistics, finance, healthcare, education, government, banking, FinTech, energy, and public organizations. This article highlights the intersection between Earth Day’s ambitious renewable energy goals and the critical roles cybersecurity and cloud infrastructure play in achieving them.

Image Source: Shutterstock
Understanding the Theme: OUR POWER, OUR PLANET
The Earth Day 2025 theme, OUR POWER, OUR PLANET, is a powerful call to action emphasizing collective responsibility to embrace renewable energy. To meet the challenge set by EarthDay.org—tripling global clean electricity generation by 2030—the international community must rapidly expand solar, wind, hydroelectric, geothermal, and other renewable sources.
- The pathway to success involves widespread engagement through:
- Education and awareness about renewable energy.
- Advocacy for strong energy policies.
- Mobilization of resources and community participation.
Digital platforms, driven by secure and scalable cloud infrastructures, serve as critical vehicles for achieving these goals, allowing widespread dissemination of information, secure online collaboration, and efficient management of renewable energy projects.
The Role of Cloud Infrastructure in Achieving Sustainability Goals
Cloud infrastructure plays a critical role in achieving global sustainability targets by enabling efficient, secure, and scalable management of digital resources. This technology underpins many innovative solutions that can significantly reduce the environmental impact across various sectors.
Reducing Energy Consumption
Cloud computing significantly reduces energy consumption compared to traditional data centers. Leading cloud providers, such as Google and Microsoft, utilize large, centralized data centers optimized for energy efficiency, often powered by renewable energy. The consolidation of data services reduces energy waste by increasing the utilization rate of servers and minimizing idle infrastructure.
Additionally, advanced virtualization technologies further improve efficiency, dramatically reducing the physical hardware requirements and resulting in substantial energy savings. Organizations adopting cloud services can substantially decrease their carbon footprint and operational costs, aligning with global sustainability objectives.
Building on this, solutions like Sangfor’s aDesk VDI and HCI take energy efficiency a step further by enabling centralized, virtualized IT environments that minimize hardware use and power consumption. By streamlining infrastructure and supporting remote work, these technologies help businesses operate more sustainably while enhancing agility and reducing costs—making them a practical path toward greener IT.
Enhancing Renewable Energy Integration
Cloud platforms are essential for managing renewable energy infrastructure. Smart grids rely heavily on cloud computing for processing large data volumes from IoT sensors, predicting power loads, and balancing supply from renewable sources. This efficient management ensures reliable power distribution and facilitates the integration of intermittent renewable sources like solar and wind into the power grid.
Remote Collaboration and E-learning
By enabling secure, remote work and learning environments, cloud services drastically reduce travel needs and associated carbon emissions. Digital classrooms and virtual meetings hosted in the cloud eliminate the necessity for extensive physical resources, aligning with sustainability targets.
Moreover, cloud solutions provide scalable and flexible learning environments accessible globally, removing geographical barriers and fostering greater inclusivity. Enhanced collaboration tools integrated into cloud platforms facilitate seamless information exchange, productivity, and innovation, further reinforcing environmental and educational goals.
Cybersecurity: Safeguarding the Transition to Renewable Energy
As we increasingly rely on digital systems for renewable energy management, cybersecurity becomes an indispensable component. Secure digital environments ensure the resilience and reliability necessary for a smooth and effective transition to renewable energy.
Protecting Critical Infrastructure
The shift to renewable energy involves integrating complex digital systems, which introduces cybersecurity risks. Cybersecurity safeguards critical energy infrastructure from cyber threats. A breach in renewable energy infrastructure—such as solar plants, wind farms, or smart grids—could disrupt power supplies and erode public trust. Incidents such as the Colonial Pipeline cyberattack demonstrate the potential disruption and environmental harm caused by vulnerabilities in digital systems.
Secure digital infrastructure ensures reliability, continuity, and resilience essential for renewable energy grids and management systems. Robust cybersecurity is imperative to protect against cyber-attacks, ransomware, and espionage. Implementing multi-layered security protocols, regular security audits, and advanced threat intelligence solutions can significantly mitigate these risks, ensuring that critical renewable energy infrastructure remains operational and secure.
Ensuring Reliable Operations
Secure monitoring and proactive threat detection ensure uninterrupted renewable energy operations. Reliable cybersecurity practices enable early identification and mitigation of vulnerabilities, significantly reducing downtime and maintaining stable power supplies. Cybersecurity's role extends beyond protection to fostering resilience, allowing rapid recovery from potential cyber incidents. This reliability is crucial for the widespread acceptance and integration of renewable energy solutions, ensuring that clean energy systems can sustainably meet global energy demands without disruptions.
Data Privacy and Compliance
In sectors such as healthcare, banking, fintech, and education, maintaining data privacy is critical. Strong cybersecurity practices ensure compliance with data protection regulations, building consumer confidence in digital services and further enabling remote service delivery, reducing environmental impacts. Compliance frameworks such as GDPR and PDPA require stringent data management practices, which robust cybersecurity ensures. By safeguarding sensitive data, cybersecurity helps these sectors avoid costly breaches and legal repercussions, fostering an environment conducive to sustainable digital innovation.
Industry Spotlight: Cybersecurity and Cloud Driving Sustainability
Each sector faces unique sustainability challenges; adopting robust cloud infrastructure and cybersecurity strategies enables significant strides toward meeting environmental objectives.
Logistics and Supply Chain Management
Cloud-based platforms enable secure, transparent logistics operations, optimizing routes, improving efficiency, and reducing fuel consumption. Secure blockchain technologies ensure goods' traceability, supporting regulatory compliance and sustainability reporting. Additionally, predictive analytics via cloud infrastructure aids inventory optimization, reducing waste. Enhanced cybersecurity safeguards logistics operations against data breaches or service interruptions, maintaining continuous efficiency and sustainable operations, even under threat conditions.
Finance and Banking
Secure cloud platforms facilitate digital banking and fintech solutions, minimizing physical branches, paper waste, and associated emissions. Cybersecurity measures protect financial transactions, ensuring integrity and building user confidence in digital platforms. Additionally, cloud-enabled financial solutions enable wider access to green finance initiatives, sustainable investments, and financial inclusion, empowering both institutions and individuals to engage more directly in sustainable economic practices.
Education
Cloud-based education platforms significantly reduce campus environmental footprints by facilitating remote learning, eliminating physical infrastructure demands, and paper usage. Cybersecurity ensures safe and secure online educational experiences, protecting sensitive student and institutional data. Additionally, scalable cloud solutions enhance resource sharing and collaborative learning, increasing educational equity and access to high-quality resources, supporting global sustainability through education.
Healthcare
Cloud-hosted telemedicine drastically reduces patient travel emissions, contributing directly to sustainability targets. Cybersecurity measures protect sensitive patient information, maintaining compliance and fostering trust in digital healthcare services. Cloud solutions also enhance the efficiency of electronic health records (EHR) systems, reducing resource waste and administrative burdens, further supporting healthcare sustainability goals.
Government and Public Sector
Governments utilizing cloud infrastructure securely offer digital public services, significantly reducing emissions from traditional administrative processes. Cybersecurity fortifies these services against disruptions and secures citizen data privacy, enhancing public trust. Additionally, secure cloud solutions enable real-time data analytics and smart-city initiatives, facilitating efficient resource use, better urban planning, and transparent governance aligned with sustainability targets.
Energy Sector
Smart energy management through cloud computing enables efficient grid monitoring, renewable energy integration, and predictive maintenance, maximizing renewable usage and minimizing downtime. Strong cybersecurity measures ensure energy infrastructure resilience, protecting against potentially catastrophic cyber incidents. Cloud platforms facilitate rapid scalability and agility necessary for incorporating growing renewable energy capacities and adapting dynamically to fluctuating demand and environmental conditions.
Integrating Cybersecurity & Cloud Infrastructure for Sustainability
To effectively leverage cloud and cybersecurity solutions for sustainability, organizations should:
- Adopt Renewable-Powered Cloud Providers: Select cloud providers committed to renewable energy and sustainability certifications such as ISO 14001 or LEED.
- Enhance Cybersecurity Frameworks: Implement comprehensive cybersecurity strategies using frameworks like NIST Cybersecurity Framework or ISO 27001 to secure cloud operations.
- Promote Remote Operations: Encourage remote work and digital collaboration, reducing carbon emissions from commuting and physical office use.
- Implement Sustainable IT Practices: Adopt circular economy principles for IT infrastructure, including recycling and responsible disposal of electronic waste.
- Continuous Education and Awareness: Regularly educate employees and stakeholders about cybersecurity best practices and sustainability goals, fostering a culture of environmental stewardship and digital security.
Looking Ahead: Beyond Earth Day 2025
Achieving Earth Day 2025’s ambitious renewable energy goals demands sustained global collaboration and technological innovation. Emerging technologies such as artificial intelligence, quantum computing, and advanced cybersecurity solutions will continue playing pivotal roles. AI-driven data analytics in cloud environments optimize energy usage, predictive maintenance of renewable energy infrastructure, and real-time cybersecurity threat detection.
Global initiatives like the Paris Agreement and the European Green Deal illustrate the necessity for comprehensive international cooperation. Stakeholders across sectors must commit not only to technological innovation but also to robust cybersecurity and resilient cloud infrastructures as essential components of sustainability strategies.
Conclusion: Uniting Cybersecurity, Cloud, and Sustainability
Earth Day 2025, themed OUR POWER, OUR PLANET, calls upon every individual and organization to actively contribute to a sustainable future. Cybersecurity and cloud infrastructure form foundational elements enabling secure, reliable, and efficient renewable energy adoption and sustainability across vital industries. By leveraging secure cloud computing and prioritizing cybersecurity, we collectively strengthen our resilience against environmental and cyber threats.
This Earth Day, let us pledge to take action—educating, advocating, and mobilizing resources—leveraging secure digital infrastructure as powerful tools in the global effort to triple renewable energy capacity by 2030. OUR POWER is collective action; OUR PLANET depends on our commitment.
Together, through secure and sustainable technology, we can shape a resilient, cleaner, and greener future for generations to come.
Frequently Asked Questions
Cybersecurity protects renewable energy infrastructure from cyber threats, ensuring reliable and secure operations of smart grids and energy management systems.
Cloud computing consolidates IT resources in energy-efficient data centers, significantly reducing carbon emissions and supporting renewable energy use.
Yes, cloud infrastructure reduces physical resource requirements, utilizes renewable energy efficiently, and minimizes electronic waste.
Cybersecurity safeguards telehealth systems and patient data, enabling secure remote healthcare delivery that reduces travel and facility-related emissions.
By choosing renewable-powered cloud services, enhancing cybersecurity frameworks, and adopting sustainable IT practices, organizations can effectively align digital security with environmental objectives.